Bring Your Own Device (BYOD) is more complex than most people know, read further to learn… . .
Keywords for this free course: . motivation, engagement, heroes, Security-Scouts, critical thinking, stay out of the box, adapt to new technologies, be aware of the malware, nobody is perfect, knowing the dangers and risks, responsibility, responsibility of School, responsibility of IT-Admin, responsibilities of BYOD users, Apple insecurity, Insecurity of Apps, Principals responsibilities, Mobile Device Management, risks of BYOD, BYOD-Policy, IT-Security Infrastructure, Teacher-Parents Meeting, Cyberwar, Cyberwarfare, Government, Internet-Safety, IT-Security knowledge basics...
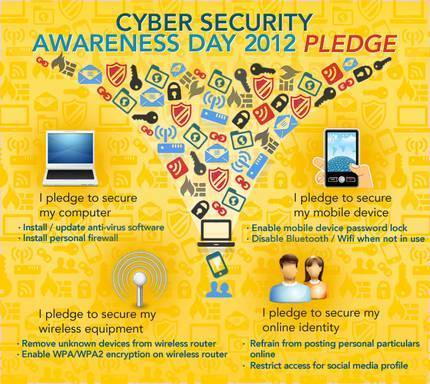
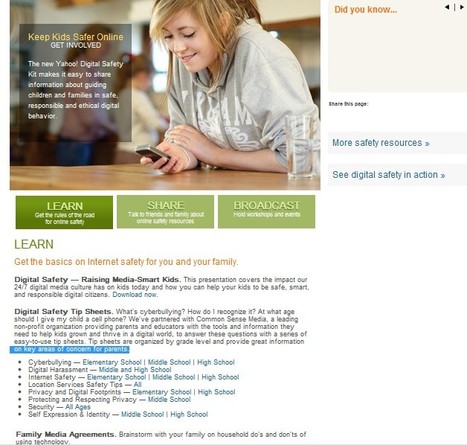
The weakest link in the Security Chain is the human! If you don’t respect certain advice you will get tricked by the Cyber-Criminals!
=> NOBODY is perfect! A security by 100% doesn’t exist! <=
Read more:
http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/



 Your new post is loading...
Your new post is loading...




















![Cisco: The Biggest Mobile BYOD Deployment Around? [Slides] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/979Kz0MNTSPBQDYgcyqzhzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)